Can your company grow on recurring revenue if your payments are not safe?
No! Although people long for comfort, they do not want to risk their bank accounts and personal data.
The subscription economy is growing rapidly and the key reason for this growth is comfort. Since OTT streaming and playing games to listening to songs and receiving food sets, models based on subscriptions revolutionized customer interactions and payments.
But making payments is still a risk! Do you remember this fitness application, missed recovery and unused application? These are the exact opportunities that cyber criminals wait for they crawl and steal sensitive data.
Since they receive an average of 17 paid media subscription subscriptions for the millennium, concerns about cyber security increase and become a primary factor for long -term business success. In this blog post, we look at the role of subscription economies and the role of cyber security in it.
Understanding an economy of subscription
The subscription economy is a business model in which customers are moving from traditional one -off purchases to repeating payments for access to the product or service after a predefined period. It can be for a week, month, six months or even a year.
The term concerns a wider transition to the market towards the subscription -based business models. Subscription -based economic characteristics are:
- Repetitive income: Businesses rely on repeating payments, generally per month or annually. A fixed number of users make payments, leading to predictable and robust income flows. You can even predict future financial needs and specify business strategies.
- Temporary approach: Subscription customers are not interested in ownership of the product; They only want a temporary approach to fulfilling their needs. Subscription models offer flexibility to suspend subscriptions at the moment.
For example, Netflix is working on a subscription -based model. It receives recurring payments from users and in return allows access to streaming services for a limited period of time.
Source
- Adaptation: Customers accept traditional products as they are without getting the opportunity to adapt them. However, you can adapt your package to your package by including the necessary services and tools.
For example, Hubspot, Saas, offers its users adapted plans to access marketing software. They offer two plans:
- Marketing Hub Professional: for small marketing teams.
- Hub Enterprise: for large marketing organizations.
Based on the size of your business, select the plan and apply the benefits.
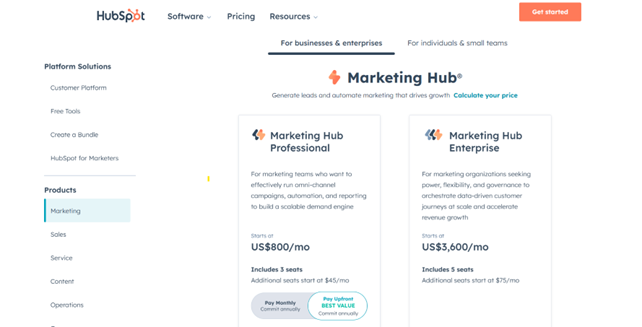
Source
- Customer satisfaction: Re -engagement of customers after purchasing is time consuming and unproductive. Since subscription models work on regular payments and immediate services, customers feel satisfied and engaged, which supports confidence.
For example, a news website, such as The Los Angeles Times, offers a digital approach based on subscription to the latest news and updates. The site even warns users of message violations, keeps them up to date and connected.
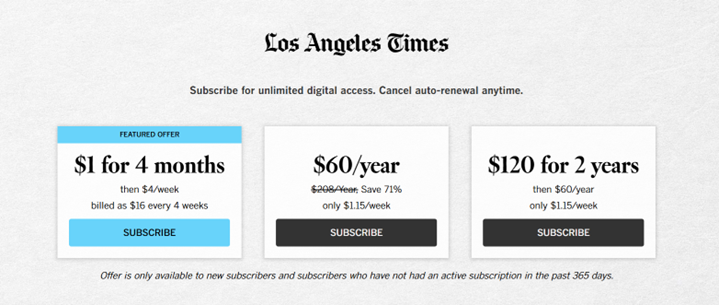
Source
Speaking of these digital platforms, one thing raises concerns – the threats of cyber security and the impact on the payment gateway. Let’s understand the connection between cyber security and subscription.
Cyber Security: Hidden backbone subscriptions
The subscription economy is expected to reach USD 34851 billion with $ 59.5%by 2029. With this rapid growth, the model becomes susceptible to cyber security threats and warns businesses to take preventive steps.
Even customers prefer to make payments and share personal data with platforms that have a protective layer to secure data. Therefore, effective cyber security is not only pleasant; It is an irreplaceable factor for building trust and credibility.
There are three pillars of cyber security:
Preparation
- Elaboration of a robust plan of response to incident
- Protocols to ensure clear communication in case of violation
- Regular audits and threat evaluation
Organization
- Use of two -factor verification across platforms
- Roll -based control frames introduction (RBAC)
- Strict security policies with frequent evaluation
Awareness
- Organization of Security Educational Programs
- Performing phishing exercises
- Well -defined safety panties
Subscription business is not only about the validity of the monitoring plan. Cyber security protocols should be considered to avoid fraud and customer confidence. Let’s explore why cyber security of the backbone of the subscription of business is:
1. Shared access weakens verification
Access to multiple users will open a window for cyber criminals. For example, if a friend, a colleague or a member of the family with whom you shared access to phishing fraud may endanger sensitive data such as banking data and authorization of all users associated with this particular account.
A common scenario is when team leaders share access with more team members without ensuring correct verification.

Source
Solution: Deployment of one login (SSO), two -factor verification (2FA) and multi -factor verification (MFA) to strengthen access control. You can also use professional time monitoring software to monitor user activity and detect unauthorized access.
2. Risking payment data
No matter what subscription customers they take, they must share their payment details with your platform. In the case of cyber attack, payment data of all users are at risk. If the customer uses the same method of payment on multiple platforms, then one violation can reveal their entire financial information.
Solution: Offer payments such as virtual credit cards, purses and alternative payment methods (APMS) to create a bridge between the bank account and the platform. You also have to.
3. Subscription fraud
A notorious cyber attack tactic is to send false alerts of the recovery and notification of an account suspension via phishing e -mails. These e -Mails carry links to fake websites imitating the original service. Users are cheating on sensitive banking data, which provides full access to their bank accounts.
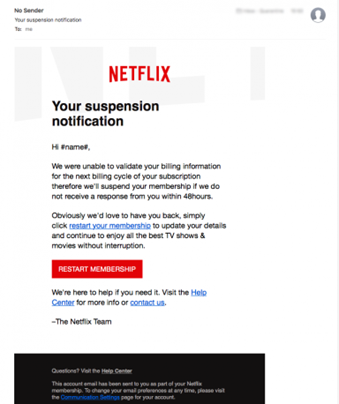
Source
According to a survey conducted by cyber security experts, on average, 31,000 phishing attacks take place on an average of the formal business e -mails.
Solution: Book users about fake links and use E -Mail filtering tools to detect phishing messages. You can also use the AI -driven session monitoring to send regular account updates to the user.
4. Unused subscription to invite cybernetic criminals
Forgot to subscribe to a streaming account is fine, but not deactivation is a problem. Cyber attackers use dormant accounts to access login data and digital fraud. A common tactic is the encirclement of credentials, where attackers collect data on leakage of login data from historical violations to log in to multiple platforms.
Age accounts are an easy goal because they have weak passwords and are not monitored. According to an OKTA state of Secure Identity 2022 report, 34% of prey accounts were on attacks on stuffing on their platform.
Solution: Use tools to manage subscriptions to monitor unused accounts and cancel subscriptions. Keep fewer sleeping accounts to minimize the risk of security disruption.
5. Unauthorized registration
A team member can apply for a prepaid CRM tool without approval. This scenario is called Shadow IT, which increases the chances of cyber attacks and harms compliance. Shadow IT offers direct access to malware and errors to stole vital client data.
The shadow increased to 56% in the SaaS industry because companies usually use about 270-364 applications to solve different tasks.
Source
Solution: Take advantage of the cloud subscription tools to centralize account management and allow IT experts to strengthen safety protocols. Also, the detection of fraud with AI-LED can identify suspicious registrations and block access.
Challenge of Payment Complexity in subscription model
Although subscription models generate stable income and repetitive income flows, along the way they also represent the complexity of payments.
Some common challenges in the subscription model include:
1. Consistency with regulation
To ensure data protection, the operation of a subscription -based business model requires strict adherence to GDPR and PCI DSS regulations. For example, if you run the start of technology, compliance with multiple legal requirements becomes mandatory for worldwide scaling.
Failure to observe often leads to stiff fines of up to $ 100,000 a month (for non -compliance with PCI DSS).
2. Maintaining the customer
In recurring income models, maintaining customers is the most important part, as the preservation rate determines the income. This includes a significant amount of investment in custom -made content to customers and a transparent payment process.
Factors such as unclear price, uninformed prices and unsuccessful payments, reduce customer satisfaction and increase the excess rate. Therefore, a user -friendly billing process and a self -service portal need to improve customers.
3. Strong payment servers
Businesses must cooperate with addicted payment servers to minimize the scenarios of unsuccessful payments. To develop strategies for solving expired credit cards, insufficient funds and server bankruptcy. These strategies may include automated reminders, repetitions of payments and more payment options.
For example, Saas can integrate into international transaction gates to minimize the decline in payments.
4. Store data
In order to collect recurring payments, businesses are stored by banking data of their customers for smooth transactions. However, the challenge is the storage of sensitive data. Infringement of violation payments may lead to substantial money losses and legal sanctions.
Payment information is the most anticipated data for committing fraud and sales on a dark site.
Integration of simplified and secure payment systems
The introduction of secure payment systems (SPS) is essential for each trading model based on subscription. SPS provides secure transaction lines in cloud spaces that guarantee safe payments, alleviate fraud and payment failure.
The key elements include:
- Encryption
- Token
- Payment gateway
- Mfa
- Digital wallet
- PCI DSS Compliance
The combination of all these elements prevents fraud and offers a satisfactory user experience. With people who resorted to online payments and digital products or services, the integration of simplified SPS has become critical. Let’s understand this with an example:
Amazon, leading online retail store, implements tokenization into its payment process. For example, when you make a transaction with Amazon Payment Services, it generates a token containing your card information. This ensures that the card data is not stored on servers.
Video
Now, whenever you return, just enter the three -digit security code and complete the token. Amazon also uses this token to process recurring monthly payments and ensure that sensitive card data are never stored on the web.
Payment risks are therefore minimized and income flows are continuous.
Secure your payments for sustainable subscription growth
The growing degree of adoption of trading models based on subscription requires trouble -free payment experience. This is possible when businesses go beyond comfort and focus on building trust and credibility.
Customers prefer to connect to platforms offering indisputable cyber security. Cyber security increases customer confidence and shares sensitive data without any problems. From securing payments to maintaining customers, cyber security is a pillar that supports the subscription economy.
Do you want to work with a trusted payment gateway?
Visit 2Checkout.com today and maximize your income safely from anywhere in the world.
About the author

Vineet Gupta
Vineet is the founder of 2xSAS, digital PR and construction agencies focused on results that work with brands like Hubspot, Hunter, G2 and more. He specializes in creating his own off -road campaigns and content marketing strategies that help B2B and SaaS improve their ecological operation.

